Universal Privilege Management
Our Privileged Access Management portfolio is an integrated solution that provides visibility and control over all privileged accounts and users. By uniting the broadest set of privileged security capabilities, the platform simplifies deployments, reduces costs, improves usability, and reduces privilege risks.
Endpoint Privilege Management
Achieve Least Privilege on Day One with the World’s Most Innovative Solution
Stop malicious attacks, including malware and ransomware, by assigning just-in-time privileges and controlling applications on Windows, Mac, Unix, Linux, and networked devices – all without hindering end-user productivity. Plus, bridge the gap between Windows and other operating systems by extending Active Directory’s Kerberos authentication and single sign-on (SSO).
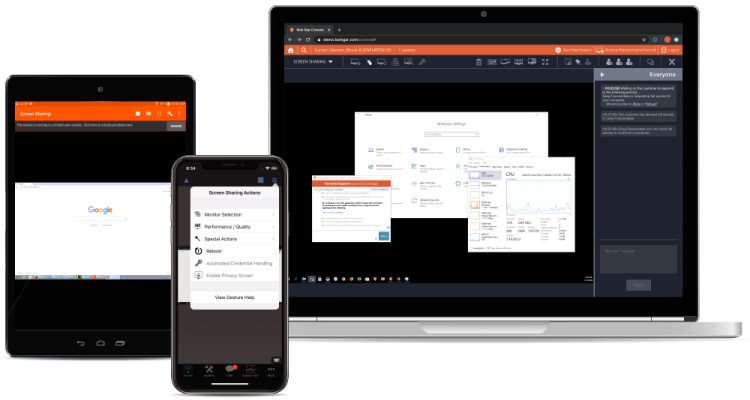
Secure Remote Access
Centrally Manage and Secure Remote Access for Service Desks and Vendors
With Remote Support, you can empower the service desk to support Windows, Mac, Linux, iOS, Android, network devices, and peripherals with one, secure tool. Privileged Remote Access allows you to secure, manage, and audit vendor and internal remote privileged access without a VPN.
Password Management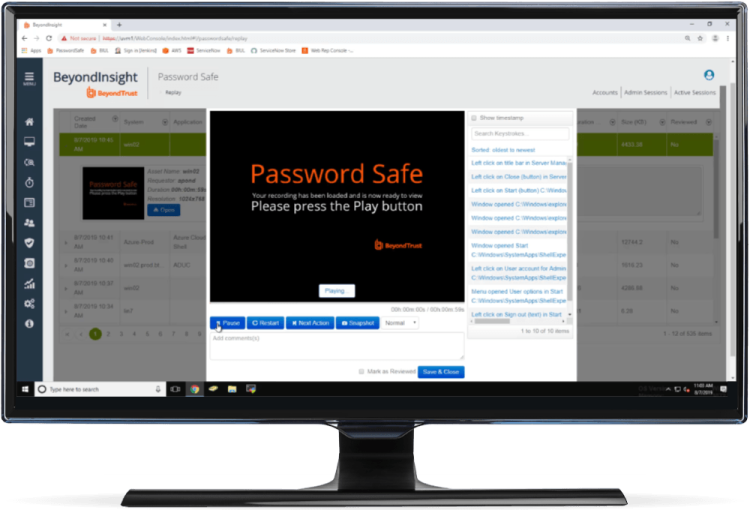
Discover, Manage, Audit, and Monitor Accounts
Password Safe lets you reduce the risk of privileged credential misuse through automated password and session management. Cloud Vault offers essential vaulting capabilities in the cloud. And DevOps Secrets Safe lets you secure and manage secrets used in DevOps environments.
BeyondInsight
Centralized Management, Reporting, and Analytics
BeyondInsight is the industry’s most innovative, comprehensive privileged access management platform that maximizes visibility, simplifies deployment, automates tasks, improves security and reduces privilege-related risks. Gain a comprehensive view of the vulnerabilities that provide doors into an environment, as well as the privileges that present corridors to sensitive assets.
The security team benefits from being able to correlate vulnerability information with user activity, while IT gains a clearer view of how privilege policies impact overall security. This fusion of asset and user intelligence enables IT and Security to collectively reduce risk across complex environments.